Ginni Rometty, IBM CEO, once said, “we need to think about security like a human immune system. Without a healthy one, you are susceptible to all kinds of diseases.”
Indeed, the increasing number of cyberattacks happening everyday is proof that the information systems of companies and government organizations aren’t “healthy,” as many have been vulnerable to all kinds of attacks, from website hacking to ransomware.
“Cybercriminals rely on exploiting known vulnerabilities to conduct their attacks – this is due to the fact that many organizations are slow to implement software updates on their corporate computers,” said Yury Namestnikov, Senior Security Researcher at Kaspersky Lab, in an email interview with UpgradeMag.com.
A new study conducted by Trend Micro reveals that cyber threats in the Philippines increased at an alarming rate of 48 percent in the second quarter of 2016 compared to the previous quarter, with the banking and finance industry mostly affected. Online attacks for online banking credentials of users in the Philippines have increased, currently accounting for 8% of online banking attacks across its client base globally.
The security firm revealed that in the Philippines, the most favored industries of cyber criminals are banking and financial services industry (FSI), followed by information and communications technology, manufacturing, and transportation.
The speed in which cybercrime is committed is also alarming. In 93 percent of cases, it took attackers minutes or less to compromise systems and data exfiltration occurred within minutes in 28 percent of the cases, according to the Verizon 2016 Data Breach Investigations Report.
Elad Ben-Meir, VP for Marketing at Israeli-based IT security company, CyberInt, notes that the Philippines is a favorite of cybercriminals because of its high exposure to social media and weak cybersecurity. Ben-Meir said that the Philippines ranks 7th in Asia Pacific for ransomware attacks, with an average of 17 attacks per day.
Ben-Meir also said that the country’s malware encounter rate is nearly double the global average at 29.1 percent.
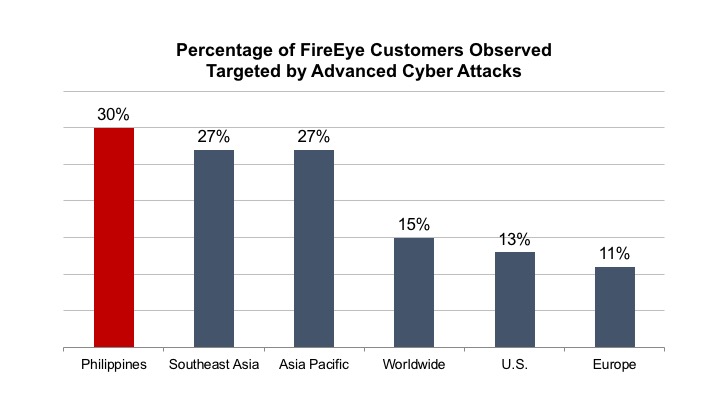
“Cyber security in the Philippines today is relatively poor,” added Bryce Boland, Chief Technology Officer for Asia Pacific of FireEye, in an interview with UpgradeMag.com. “Some organizations do an adequate job, and a select few do a good job, but most organizations remain exceptionally vulnerable to advanced cyber attacks.”
Wake-up call
One of the most highlighted incidents in the Philippines this year was the hacking of the Commission on Elections website in March which leaked the personal data of 55 million Filipino voters, putting them at risk of identity theft.
Another newsmaker which put the Philippines on the global spotlight around the same time was the Bangladesh heist. According to security experts at BAE Systems, malware was used to help an unknown attacker gain access to the Bangladesh Bank’s (BB) SWIFT payment system and reportedly instructed an American bank to transfer money from BB’s account to accounts in the Philippines. The attackers attempted to steal $951m, of which $81m is still unaccounted for.
The aforementioned statistics and incidents make Philippines one of the countries with weak information technology systems. In fact, the Philippines is among the top 50 countries with hacked services listed in the xDedic site, a global online marketplace where cybercriminals can buy and sell access to compromised servers for as little as $6 each.
The xDedic marketplace, discovered by Kaspersky Lab and which appears to be run by a Russian-speaking group, listed, in May this year, 70,624 hacked Remote Desktop Protocol (RDP) servers for sale.
“The current events highlighting the country’s vulnerabilities served as a ‘wake-up call,’ putting security at the center of every business discussion,” Luis Pineda, President & Country General Manager, IBM Philippines, told UpgradeMag.com.
Prominent threats
Citing a report from FortiGuard Labs, Jeff Castillo, Fortinet Philippines Country Manager, said there are three prominent threats that are causing damaging impact to most institutions and enterprises in the Philippines: exploits, botnets, and malware.
Castillo explained that hackers cast and install automated systems and software tools to exploit application vulnerabilities, and worse, to compromise corporate data.
“Surprisingly, the report revealed that utilizing exploits has dropped by 52 percent in the Philippines. Some exploits, however, are still rampantly used by hackers like SSH server key exchange overflow, WordPress pingback Dos and TCP split handshake exploit,” said Castillo.
Andromeda, on the other hand, is the top botnet in the country, followed by Zero access, H-worm, and Crypto botnet traffic.
The report also showed that 2016 opened a new era for more android malicious apps like WM/TrojanDownloader.9BB7!trend and MS Windows Word Macros(WM). For example, Triada, another top mobile malware in the country redirects the money used in in-app purchases to the hacker. This Trojan modifies and integrates itself to a system, making it easier for threat actors to conduct their malicious operations.
According to Symantec’s latest Internet Security Threat Report (ISTR), the biggest security risks to companies today are: explosion of zero-day vulnerabilities; multiple attacks; and the increasing number of companies choosing to hold back critical details of a breach.
“2015 saw some of the largest data breach made public, but more companies are choosing not to reveal the full extent of the breaches they experienced,” says Peter Sparkes, Symantec Senior Director for Cyber Security Services for Asia Pacific and Japan.
“This disturbing trend could pose more problems to companies that hold back critical information. Transparency is critical to security. By hiding the full impact of an attack, it becomes more difficult to assess the risk and improve security posture to prevent future attacks.”
Other IT security threats identified by security experts interviewed by UpgradeMag.com are cyberespionage, intellectual property theft, reputational damage, fraud, and disgruntled employees.
An IBM study unveils that 70% of CxOs think rogue individuals make up the largest threat to their organizations. The reality is that 80% of cyberattacks are driven by highly organized crime rings in which data, tools, and expertise are widely shared, according to a United Nations report.
A breach can also be very costly, depending on the extent of damage caused. The average budget required to recover from a security breach is US$551,000 for enterprises and $38,000 for small and medium sized businesses, according to a global report released by Kaspersky Lab.
Conducted in cooperation with B2B International in 2015, the survey reveals the most expensive types of security breaches are employee fraud, cyber espionage, network intrusion and the failure of third party suppliers.
Myla Pilao, Director of Core Technology Marketing at Trend Micro, says the growth in cyber attacks in the last six months was driven by three factors: poor device control, which remains to be the successful method of attacks; social engineering, considered as the second most favored attack in the Philippines; and insider information.
Pilao pointed out that the most prominent attack that hit the Philippines in the second quarter was data-stealing malware or breaches which accounted for 41% of Philippine infections. This attack, which arises from the use of old or legacy systems, gained prominence as it victimized more local industries.
“Local businesses are also still susceptible to old-school threats like file-infecting viruses and worms that spread through removable drives,” Pilao notes
Apart from information-stealing threats, Trend Micro claimed that organizations worldwide were experiencing a rise in business email compromise (BEC) and targeted attacks. BECs are sophisticated scams carried out through business emails, while targeted cyber attacks are aimed specifically at a company, individual or software
More dangerous
According to Kaspersky Lab’s Namestnikov, the tools used to attack businesses differ from those used against home users. In attacks on corporate users, exploits for office application vulnerabilities are used much more often, malicious files are often signed with valid digital certificates, and cybercriminals try to use legitimate software for their purposes, so they can go unnoticed for longer.
“We have also observed strong growth in the numbers of corporate user computers targeted by ransomware. This also applies to incidents not classified as APT attacks, where cybercriminals merely focus on corporate users, and sometimes on employees of specific companies.
“The fact that cybercriminal groups use APT methods and programs to attack businesses takes them to a different level and makes them much more dangerous. Cybercriminals have begun to use these methods primarily to steal large sums of money from banks. They can use the same methods to steal a company’s money from bank accounts by gaining access to its corporate network,” said Namestnikov.
Namestnikov noted that cybercriminals also make use of signed malicious files and legitimate tools to create channels for extracting information. These tools include popular remote administration software, SSH clients, and password restoration software, among others.
Mitigate the threat rather than the incident
“Todays threats have become more advanced, targeted, and attackers are much more organized. As a result, the skill and knowledge required to defend from threats have gone up. Unfortunately, the Philippines does not have many expert resources to meet the skills required for security,” said IBM’s Pineda.
“One of the greatest defense against attacks is by educating employees and by creating awareness,” said Pineda. Pineda also advises companies to establish a security governance program, implement continuos security monitoring, leverage incident forensics, and utilize threat intelligence to secure their environment.
Pineda’s comment on security talent is confirmed by statistics shared by CyberInt’s Ben-Meir during a press conference to announce the company’s entry into the Philippines market. Ben-Meir revealed there are only 84 Certified Information Systems Security Professionals (CISSP) in the Philippines. In comparison, Malaysia has 275 CISSPs while the US has around 67,000.
Given the scarcity of IT security talent in the Philippines today, what then, should companies do to mitigate attacks?
“Leaders must realize they’re up against real people, not technology. Determined attackers will eventually find a way in,” comments FireEye’s Boland. “The initial focus focus should be to ensure that they can detect the attacks. After that, they should turn to effectively responding to attacks. Very few organizations get that far. A few organizations go one step further and actively hung for attackers they are not aware of, but assure are there.”
For his part, Ben-Meir advises companies to “mitigate the threat rather than the incident.” This, he said, can be done in four phases: 1) identify early stage weaponization online; 2) detect phishing tools targeting customers and employees in social media; 3) spot hacked databases for sale; and 4) monitor and investigate exploitations.
For Symantec’s Sparkes, advanced analytics is key. “Attackers are becoming more sophisticated and industrialized but companies are stuck on the same strategy,” said Sparkes in an interview with UpgradeMag.com. “In the past, analytics are effectively placed into a piece of software which a company can deploy. This used to work before. But to catch all of the advanced threats today, an organization needs to do more advanced analytics which cannot be done by software alone.”
Back to Basics
Kaspersky Lab’s Namestnikov lists the four basic strategies that reduce the possibility of a successful targeted attack:
· Use application whitelisting to help prevent malicious software and unapproved programs from running
· Patch applications such as Java, PDF viewers, Flash, web browsers and Microsoft Office
· Patch operating system vulnerabilities
· Restrict administrative privileges to operating systems and applications, based on user duties.
“Sophisticated attacks offer lucrative rewards, that’s why massive data breaches are continuously occurring. There is no silver bullet that could protect an organization perfectly. Once the malware is installed, it will be automatically controlled by cybercriminals, morph, adapt, and move freely undetected,” stressed Fortinet’s Castillo. “For optimal and powerful security, individual security products should function together as one.”
Gene Ng, Security Leader, IBM ASEAN, companies should look at their information and business critical systems from an attacker’s point of view and then ask themselves how an attacker could do the most damage.
“A big chunk of risk factors are related to the people who operate, manage or even simply use any of the organizational services or assets,” said Ng. “Make sure your security program has ownership and leadership assigned across critical business areas. By expanding accountability and awareness across the company, the underlying and enforcement of the security controls are heightened — creating a more secure business environment.”
Pineda notes that a greater willingness for businesses, government organizations, and other parties to collaborate must be achieved to elevate the Philippines’ defense against threats.
“There is a dichotomy that needs to be resolved—external parties need to do more, the government needs stronger oversight, industry collaboration must increase, and cross-border sharing must be strengthened,” said Pineda.