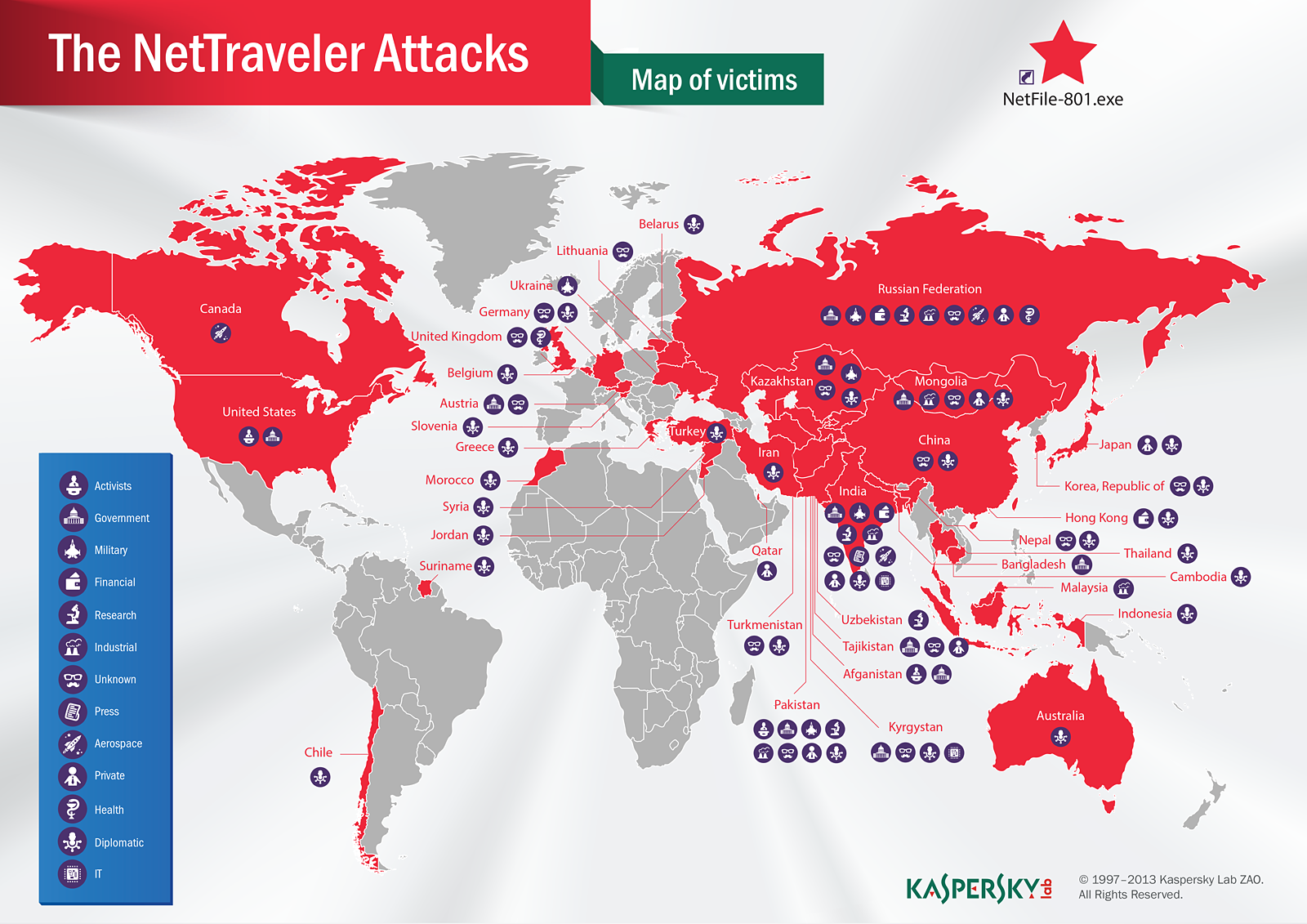
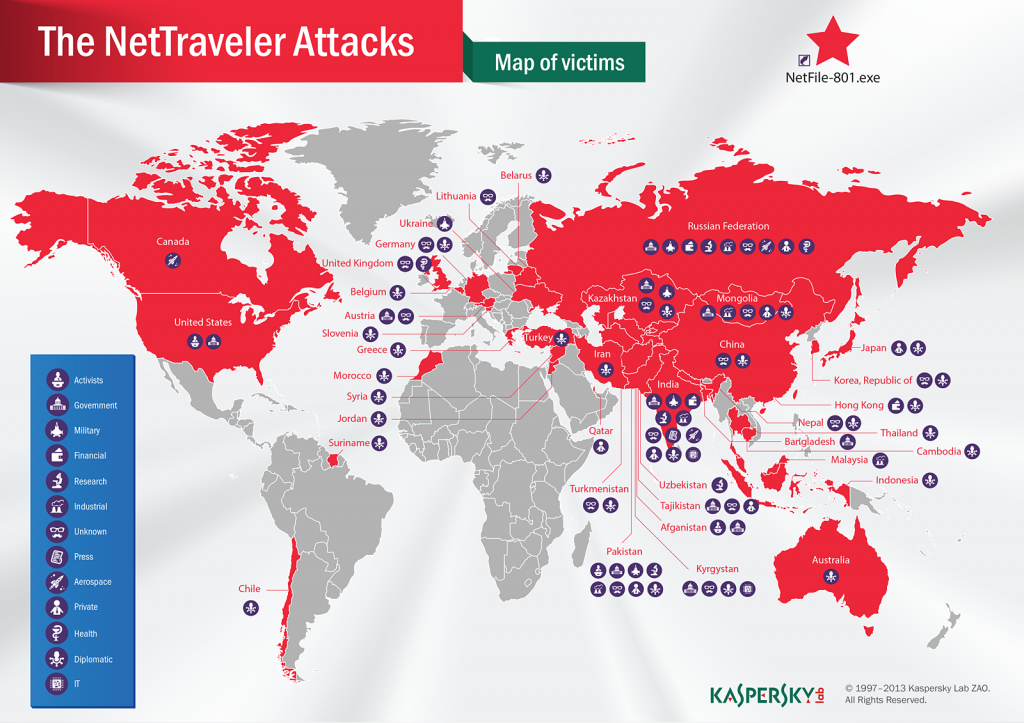
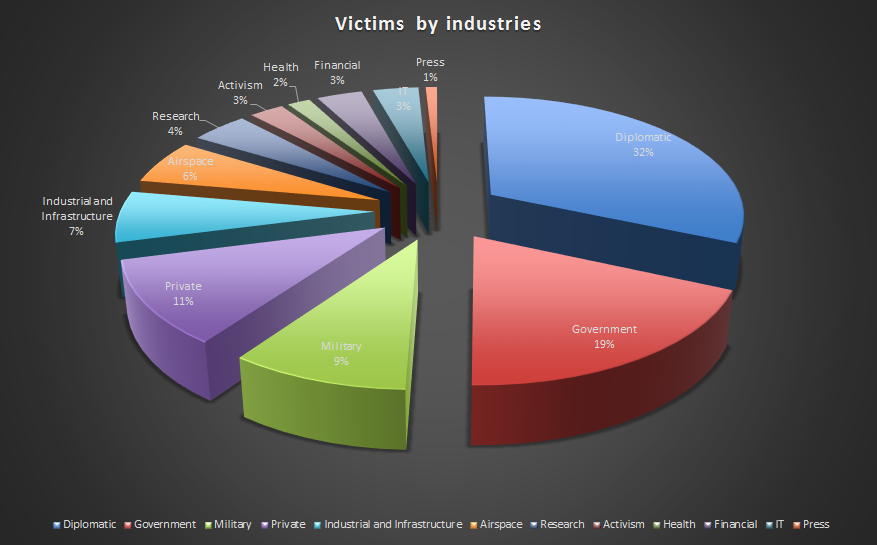
Kaspersky Lab researchers recently announced a new attack vector of NetTraveler, an advanced persistent threat that has already infected hundreds of high profile victims in more than 40 countries.
According to Kaspersky Lab, an advanced persistent threat (APT) refers to a highly precise sort of cyberattack. APT can also refer to groups, often state sponsored or well-funded in other ways, that are responsible for launching such precision attacks. The end-goal of an APT-style attack is to compromise a machine on which there is some sort of valuable information.
Known targets of NetTraveler (also known as “Travnet”, “Netfile” or “Red Star” APT) include Tibetan/Uyghur activists, oil industry companies, scientific research centers and institutes, universities, private companies, governments and governmental institutions, embassies and military contractors.
Immediately after the public exposure of the NetTraveler operations in June 2013, the attackers shut down all known command and control systems and moved them to new servers in China, Hong Kong and Taiwan. They also continued the attacks unhindered, just like the current case shows.
Over the last few days, several spear-phishing e-mails were sent to multiple Uyghur activists. The Java exploit used to distribute this new variant of the Red Star APT was only recently patched in June 2013 and has a much higher success rate. The earlier attacks have used Office exploits (CVE-2012-0158) that was patched by Microsoft last April.
In addition to the use of spear-phishing e-mails, APT operators have adopted the watering hole technique (web redirections and drive-by downloads on rigged domains) to infect victims surfing the web.
Over the last month, Kaspersky Lab intercepted and blocked a number of infection attempts from the “wetstock[dot]org” domain, which is a known site linked to previous NetTraveler attacks.
These redirections appear to come from other Uyghur-related websites that were compromised and infected by the NetTraveler attackers.
Kaspersky Lab’s Global Research and Analysis Team (GReAT) experts predict that other recent exploits could be integrated and used against the group’s targets.
The company’s experts offer the following recommendations on how to stay safe from such attacks:
- Update Java to the most recent version or, if you don’t use Java, uninstall it.
- Update Microsoft Windows and Office to the latest versions.
- Update all other third party software, such as Adobe Reader.
- Use a secure browser such as Google Chrome, which has a faster development and patching cycle than Windows’ default Internet Explorer.
- Be wary of clicking on links and opening attachments from unknown persons.
“So far, we haven’t observed the use of zero-day vulnerabilities with the NetTraveler group. To defend against those, although patches don’t help, but technologies such as DefaultDeny and Automatic Exploit Prevention can be quite effective fighting advanced persistent threats,” advised Costin Raiu, GReAT Director at Kaspersky Lab.