Keeper Security, provider of cloud-based zero-trust and zero-knowledge cybersecurity software protecting passwords, secrets, connections and privileged access, today announced the launch of password rotation, a new feature that allows organizations to securely rotate service accounts and other privileged credentials on-demand or on an automated schedule.
Keeper’s new password rotation capability enables organizations to automate the changing and resetting of system credentials including Active Directory service accounts, Azure AD accounts, AWS IAM accounts, SSH keys, database passwords, Windows local users, Linux users, Mac users and more.
Password rotation is the latest enhancement to Keeper’s next-generation Privileged Access Management (PAM) solution. Recognized as the 2023 Gold Winner by the Cybersecurity Excellence Awards and named Most Comprehensive PAM Solution by the Global Infosec Awards, KeeperPAM is revolutionizing privileged access management by providing comprehensive PAM capabilities including enterprise-grade password, secrets, and connection management in one unified platform. With the addition of automated password rotation, KeeperPAM’s capabilities continue to grow.
KeeperPAM was designed to address the cybersecurity industry’s growing demand for modern solutions that are cost-effective, easy to implement and engaging for end users. Keeper’s recent Privileged Access Management Survey: User Insights on Cost & Complexity revealed that more than half of all IT and security leaders (56%) have tried to deploy a traditional PAM solution but never fully implemented it. Of those, a staggering 92% said it was because the solution was too complex.
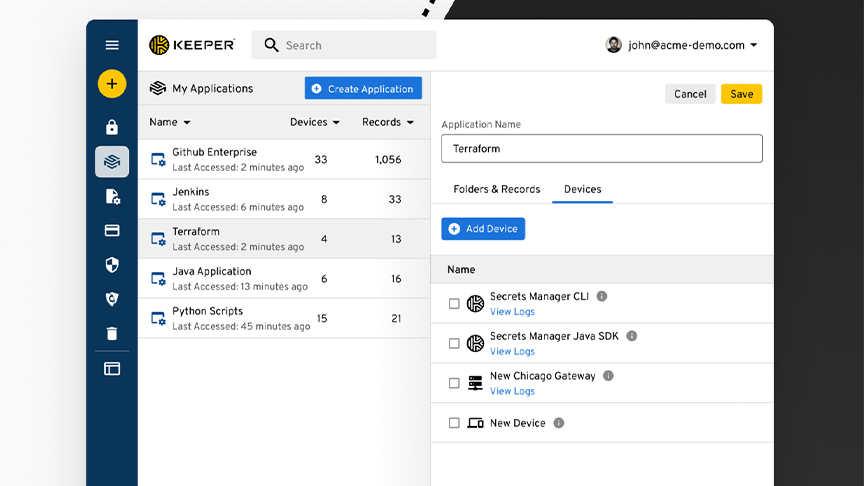
Unlike traditional PAM solutions, Keeper’s Password Rotation architecture is managed through the cloud-based vault and admin console interface, with a lightweight component that’s installed in the customer’s cloud and on-prem environment, called the Keeper Gateway service. The Gateway service and Keeper’s new multi-cloud routing infrastructure does not require security teams to make any firewall changes, and it uses native protocols for implementing rotation.
“Administrative passwords must be updated regularly and automatically to reduce the risk of password-based breaches and cyberattacks. Traditional PAM tools with password rotation capabilities are often expensive and difficult to deploy,” said Craig Lurey, CTO and co-founder of Keeper Security. “This leaves organizations that cannot afford or have never fully deployed those solutions vulnerable. We are excited to help minimize this risk with an affordable, modern and elegant solution that protects every user and every device in an organization.”
Password rotation enables customers to:
- Automatically rotate credentials for machines, service accounts and user accounts across their infrastructure, and schedule rotations to occur at any time or on-demand.
- Perform post-rotation actions such as restarting services or running other applications as needed.
- Securely store all credentials in the Keeper Vault, and control and audit access to credentials.
- Log all actions to Keeper’s Advanced Reporting and Alerts Module (ARAM) and third party SIEM providers.
- Create compliance reporting on shared privileged accounts.
Password Rotation through KeeperPAM is available through the web vault, desktop app for Windows/Mac/Linux and the admin console. The feature enables admins to seamlessly manage rotation for users and records, create gateways, configure cloud environments and enforce least-privilege access. Password Rotation as part of KeeperPAM supports Keeper’s zero-knowledge, zero-trust architecture, which always encrypts and decrypts data at the local device level.