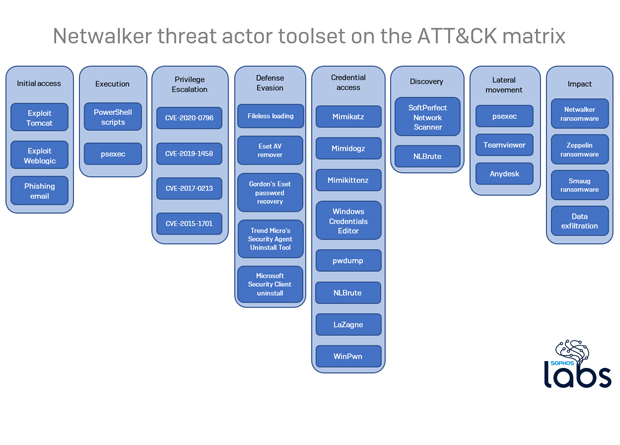
Sophos discovered a collection of third-party programs used to quietly carry out attacks while investigating the Netwalker ransomware. This includes legitimate, publicly-available software (like TeamViewer), files cribbed from public code repositories (such as Github), and scripts (PowerShell) that were created by the attackers as well.
The Netwalker threat actor has struck a diverse set of targets based in the US, Australia, and Western Europe, and recent reports indicate the attackers have decided to concentrate their efforts targeting large organizations, rather than individuals.
The tooling uncovered supports this hypothesis, as it includes programs intended to capture Domain Administrator credentials from an enterprise network, combined with orchestration tools that employ software distribution served from a Domain Controller, common in enterprise networks but rare among home users.
“Ransomware attacks nowadays are not single-shot events like WannaCry was in 2017. Cybercriminals now have well-established procedures and toolsets that they routinely use. The attacks are usually longer and multi-faceted, meaning attackers spend days or even weeks within targeted organizations, carefully mapping internal networks while gathering credentials and other useful information. In this process, they use legitimate third-party tools that may not be detected by the defenses. However, if defenders know and understand the processes and the tools that attackers are using, they can better prepare against these attacks and detect them in the early stages before the actual ransomware payload is delivered,” said Gabor Szappanos, senior director, Threat Research at SophosLabs.